Scan Sources
Viewing all connected scan sources is available in the Integrations section under the Scan Sources tab. It also provides the ability to sort by name, source type, description, and navigate to add, edit, or delete scan sources.
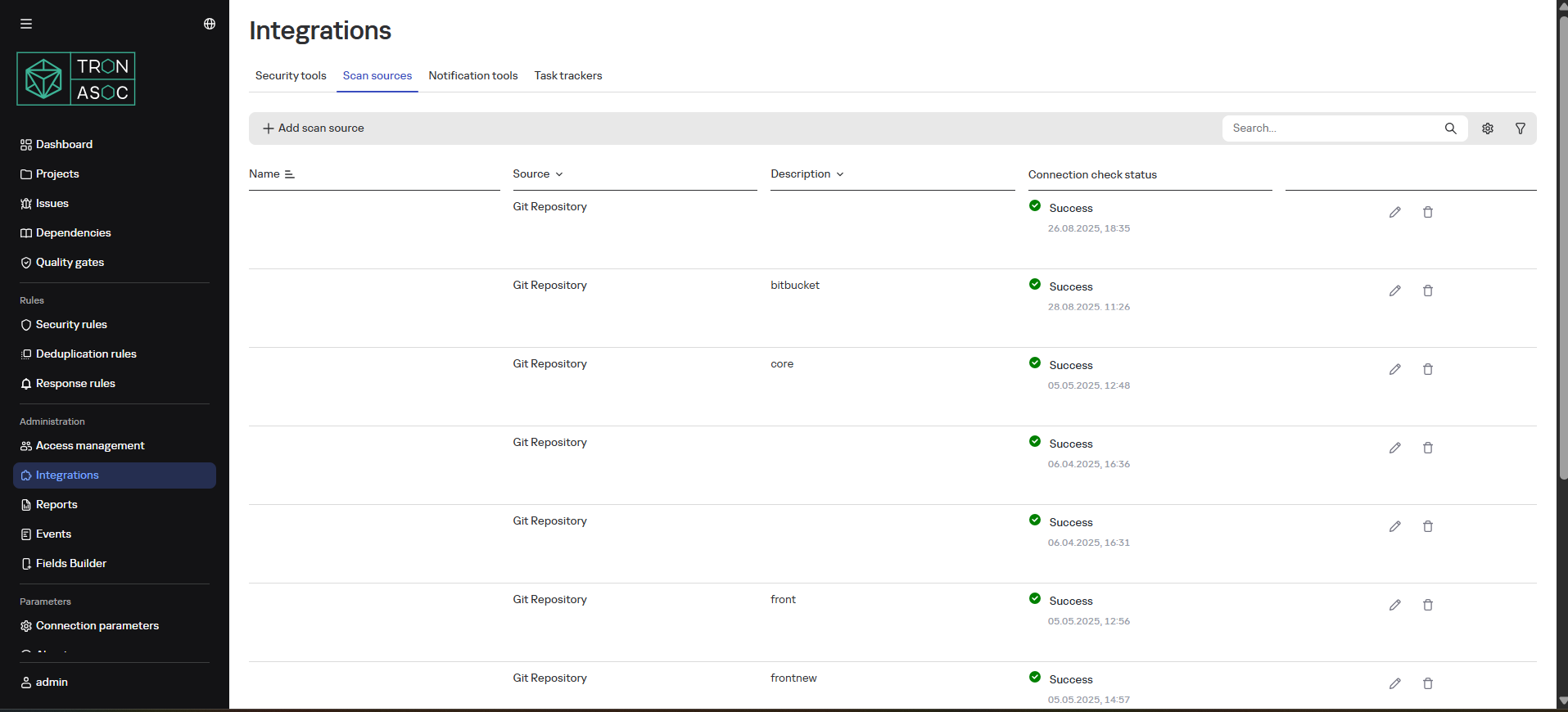
Supported Scan Sources
-
Git Repository
For a source in Git repository format, the following VCS (Version Control System) types are available:
- GitHub
- GitLab
- BitBucket (cloud and server)
- Other (other types can be connected)
infoWhen running scans using a BitBucket source, the specified port may be adjusted. For example, ssh://git@bitbucket.int.tronasoc.ru:0000/test/command.git may be formatted as https://bitbucket.int.tronasoc.ru:0000/test/command.git
cautionAfter updating TRON.ASOC to version 1.2.1 and higher, it is required to reconfigure previously added integrations with Git Repository sources where the VCS type was not configured.
Other Scan Sources:
- Nexus
- CLI Tool
- Jfrog
- Harbor
- AppUrl
Connecting a Scan Source
The set of minimum access rights for configuring scanning sources:
- View sources
- Manage sources For more details on setting up access rights, see Role Configuration.
To connect a scan source, follow these steps:
-
Navigate to the Integrations section and select the Scan Sources tab
-
Click the Add Scan Source button
-
In the opened form, fill in:
- Name
- Description
- Source (select from the dropdown list)
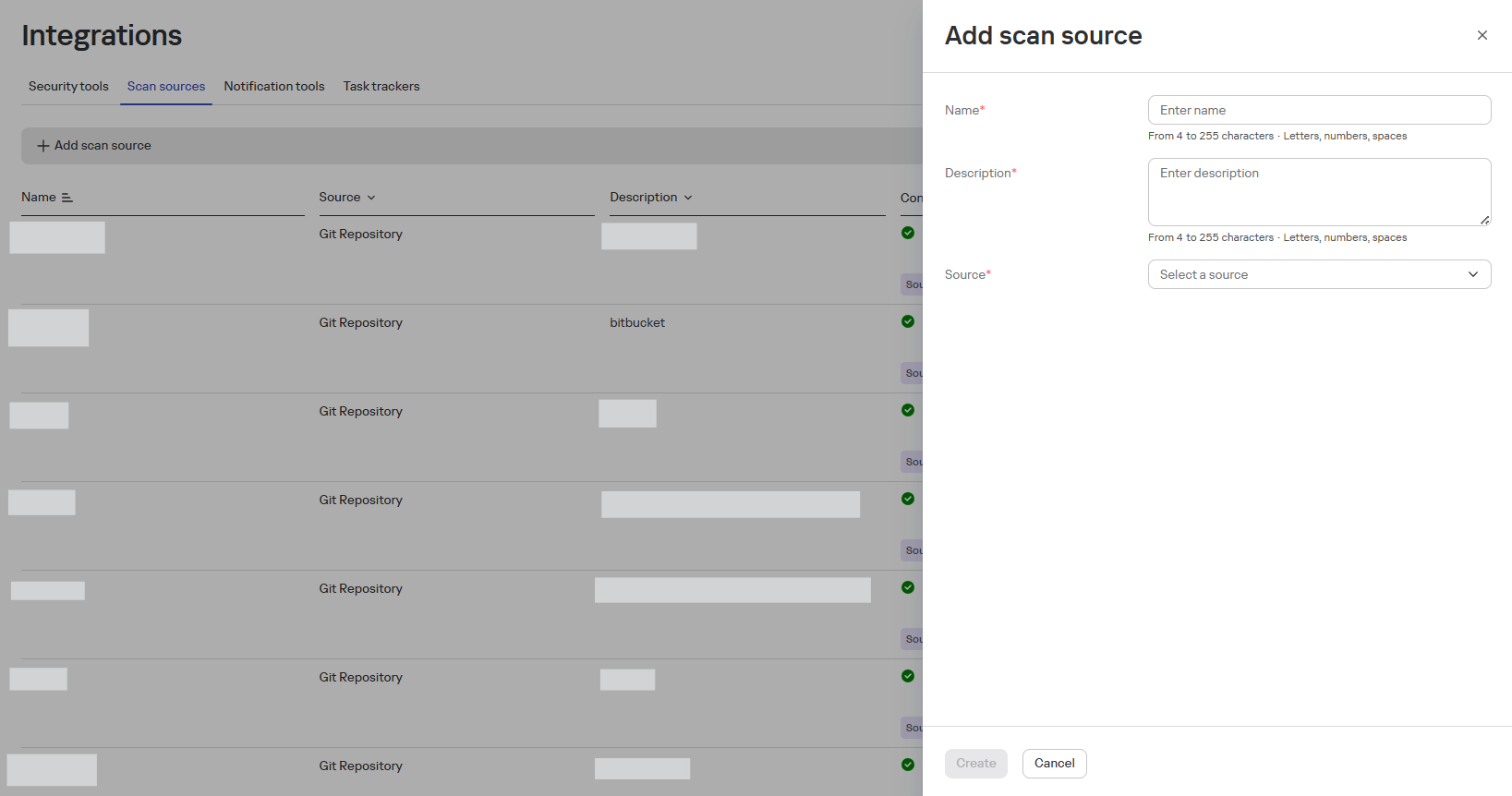
-
Fill in additional fields for the selected source:
- Source URL
- Authentication Method (optional, but required for connection testing)
- Skip test connection - when selecting this parameter, the connection with the source will not be checked before starting the scan (applied in case there is no network access to the sources)
-
Depending on the authentication method:
-
For API Token: fill in the "API Token" field
-
For Login/Password: fill in the corresponding Login and Password fields For the Git Repository source, several authentication types are available:
- API Token
- Login/Password
- Anonymous
- SSH (secure authorization method via SSH key, all SSH types are available except passphrase)
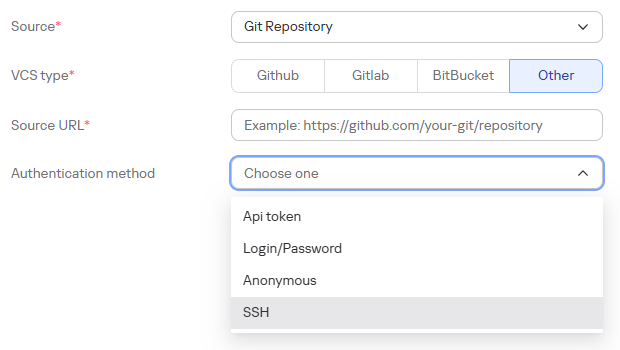
-
-
Click the Test Connection button (available when an authentication method is specified)
-
Click the Create button
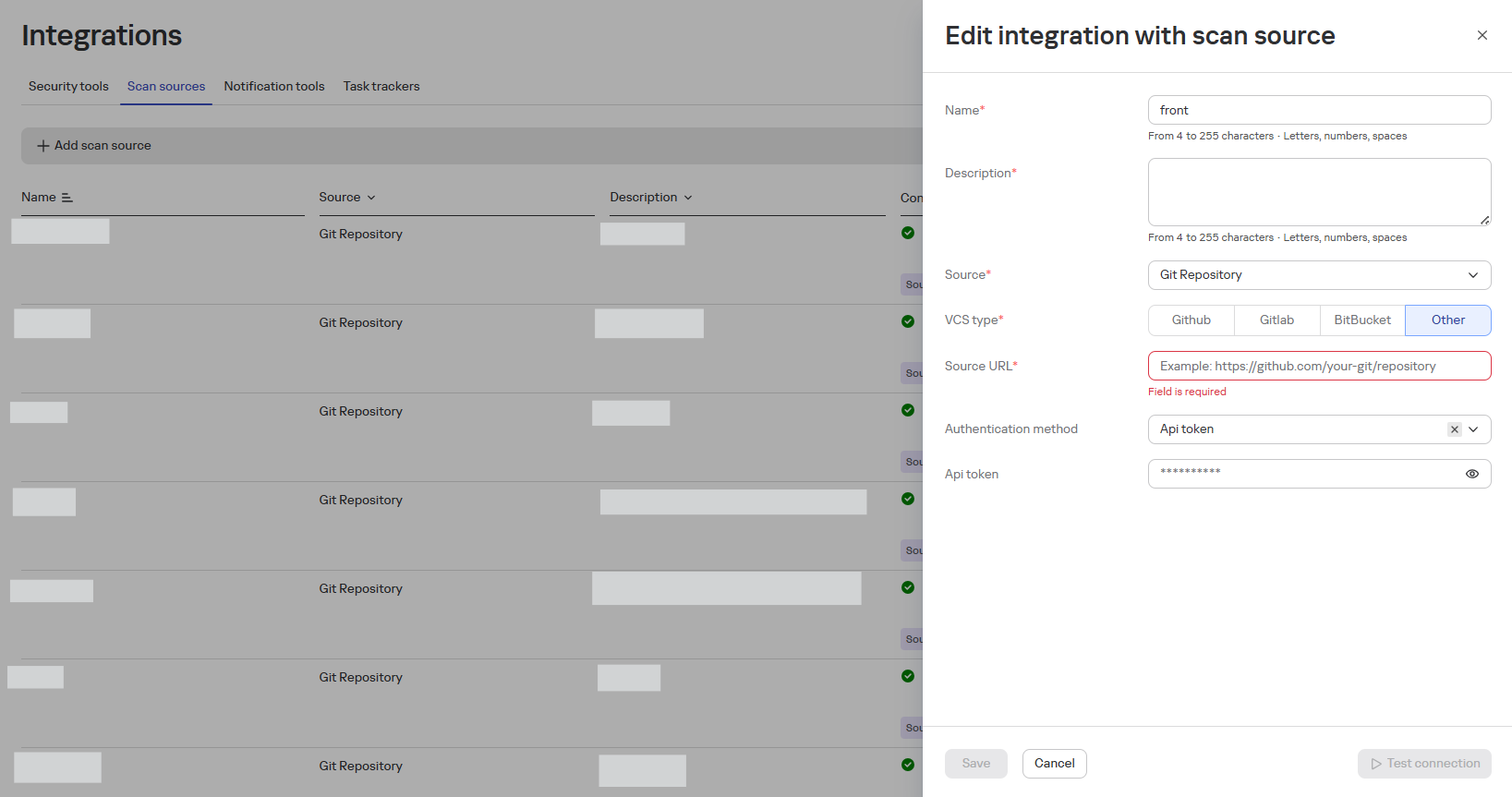
Editing a Scan Source
To edit, click the edit button in the row of the desired source.
The editing form is similar to the addition form, but the fields are pre-filled with current data.
Deleting a Scan Source
To delete a source, follow these steps:
- In the Integrations → Scan Sources section, click the delete button
in the source row
- In the opened confirmation window, click the Delete button
Combinations of scan sources and security tools in checks
The TRON.ASOC solution implements the following combinations of sources and security tools:
-
CLI tools (ESLint, Gitlab SAST, Trivy, Grype, KICS, Aqua, OWASP Dependency Track, Gitleaks) + CLI Custom source These security tools can form checks only with CLI Custom source.
-
CLI tools with the ability to run in k8s (PVS Studio, Semgrep) (within the unstable release 1.3.1) + Git Repository These tools support running. The tool runs in k8s as a job, receives data from the source, performs a security check, and returns a report with security issues.
-
KCS/Appscreener Solar DAST + Nexus/Harbor/Jfrog When creating such a check, it is additionally necessary to fill in the Source branch/tag (multiple allowed). Checks can be run, but reports can also be imported.
-
Appscreener Solar SAST/ Solar SCA/ PTAI + Git Repository When creating such a check, it is additionally necessary to fill in the Source branch/tag (multiple allowed). Checks can be run, but reports can also be imported.
-
SASTAV + Git Repository When creating such a check, it is additionally necessary to fill in the Scanning ruleset, as well as the connection between the Source branch/tag and the commit. Checks can be run, but reports can also be imported.
-
CodeScoring + Git Repository/Nexus/Harbor/Jfrog When creating such a check, it is additionally necessary to fill in the security check type - SCA, container SCA, secrets. In the latter case, it is suggested to select a secrets configuration or upload a new one. Then fill in the Source branch/tag (multiple allowed). Checks can be run, but reports can also be imported.
-
Manual tool + CLI Custom source This type of security tool can form checks only with CLI Custom source, because these tools are supported only for uploading SARIF and JSON reports.