Security Rules
The system provides the ability to create exclusion rules for working with results in the product. The Security Rules section is designed for managing security rules that apply to vulnerabilities and other security issues in projects. This allows for temporarily or permanently ignoring certain types of issues based on their priority or other criteria.
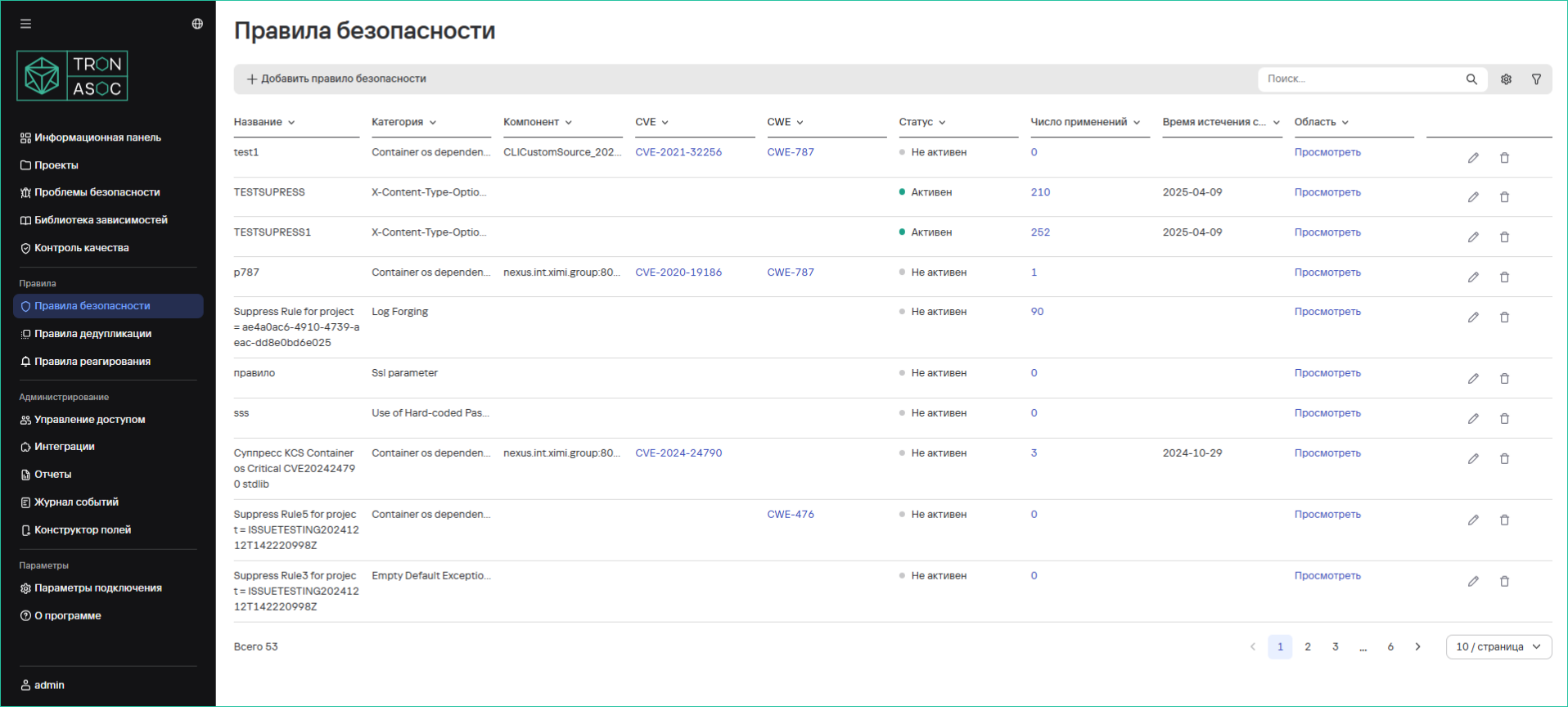
This section is intended for managing rules that apply to vulnerabilities and other security issues in projects.
Security Rules Table Structure
| Column | Description |
|---|---|
| Name | Name or identifier of the security rule |
| Category | Category of the issue to which the rule applies |
| Component | System component or repository path |
| CVE | Unique vulnerability identifier in the CVE database |
| CWE | CWE (Common Weakness Enumeration) code |
| Status | Rule activity status |
| Number of Applications | Number of times the rule has been applied |
| Expiration Date | Rule expiration time |
| Scope | Project scope |
Capabilities:
- Temporary or permanent issue ignoring
- Configuring scope (projects/repositories)
- Management by vulnerability priority/type
Creating a Security Rule
Creating a security rule is based on specified parameters. The set of parameters depends on the type of security issue. To create a rule, follow these steps:
- In the Security Rules section, click the Add Rule button
- Fill out the form with the following data:
- Name - Unique rule name
- Security Check Type
- Tool
- Issue Category
- System Component/path
- CVE identifier
- CWE code
- File/directory Path
- Vulnerability Code
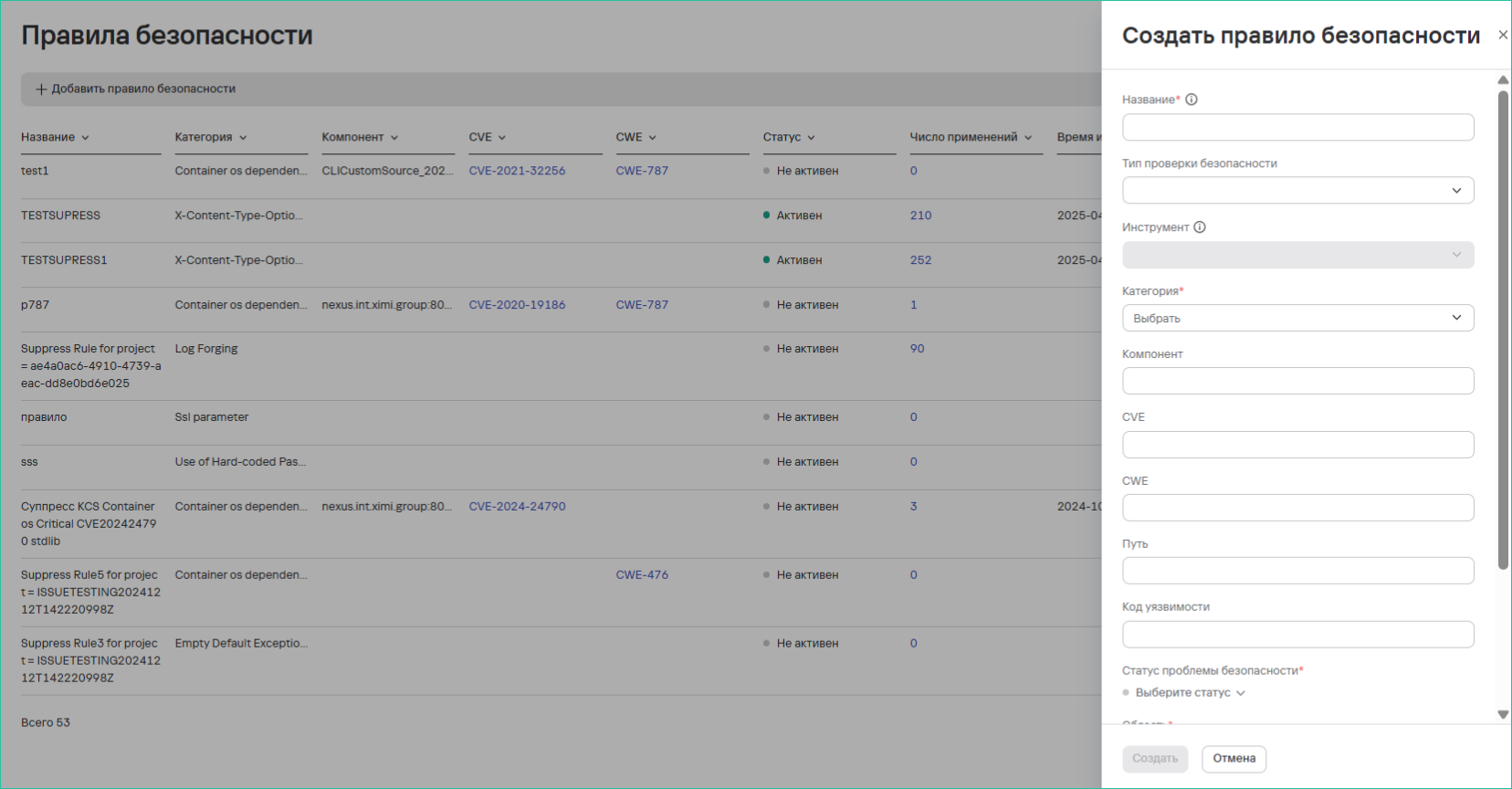
- Configure additional parameters:
- Expiration Time: fixed date or indefinite
- Security Issue Status: from available options
- Application Scope: project selection
- Status After Expiration: from available options
- Click the Create button
caution
Rules apply to all new and existing issues that match the criteria.
Key Features
- Flexible exception configuration
- Centralized vulnerability management
- Support for temporary and permanent rules
- Binding to specific projects